.png)
Accelerate security protection through a native integration platform
Prisma Cloud
Top-tier CNAPP services help customers "prevent risks and violations."
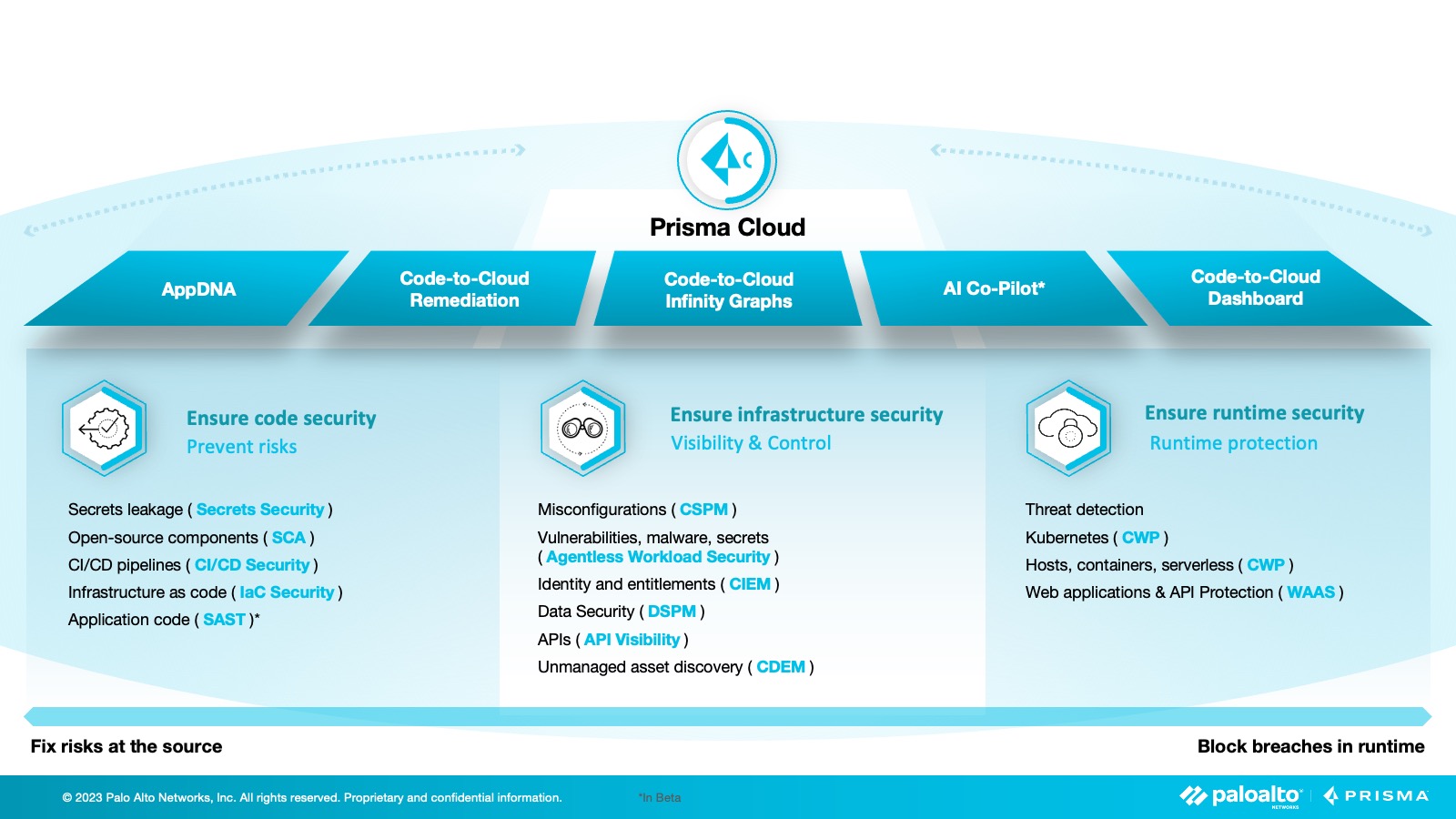
Prisma Cloud Version:
Multi-cloud Management - Compliance - Cloud Security
Comprehensive Cloud Security
Supports multi-cloud environments, including AWS, Azure, and Google Cloud. Provides comprehensive cloud workload protection, covering hosts, containers, and serverless functions.
Integrated Platform
A unified console for managing and monitoring all resources in multi-cloud environments. It integrates native cloud services to reduce complexity and enhance operational efficiency.
Automation and Compliance
Automated security and compliance scanning ensures real-time detection and remediation of potential threats. Pre-configured compliance frameworks (such as CIS, NIST, PCI, etc.) simplify compliance management.
Threat Protection
Real-time threat detection and response, using machine learning and behavioral analysis to identify abnormal activities. Provides detailed threat intelligence and risk assessment reports to help businesses respond swiftly.
Prisma SASE
Trust without boundaries, security on the go.
Industry-leading Zero Trust service provider
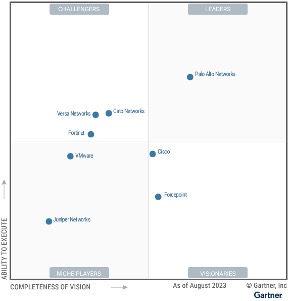
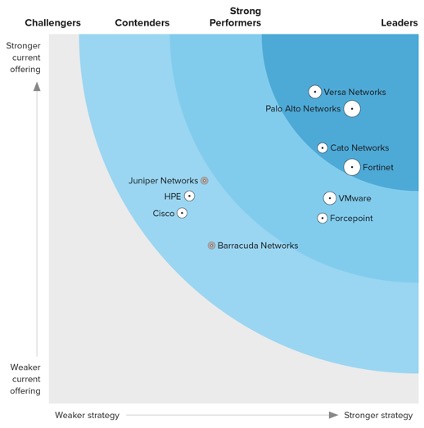
Recognized as a leader in the Gartner 2023 Single-vendor SASE Magic Quadrant
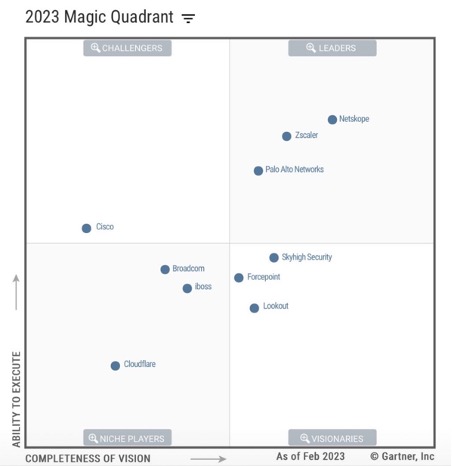
Recognized as a leader in the Gartner 2023 SSE Magic Quadrant
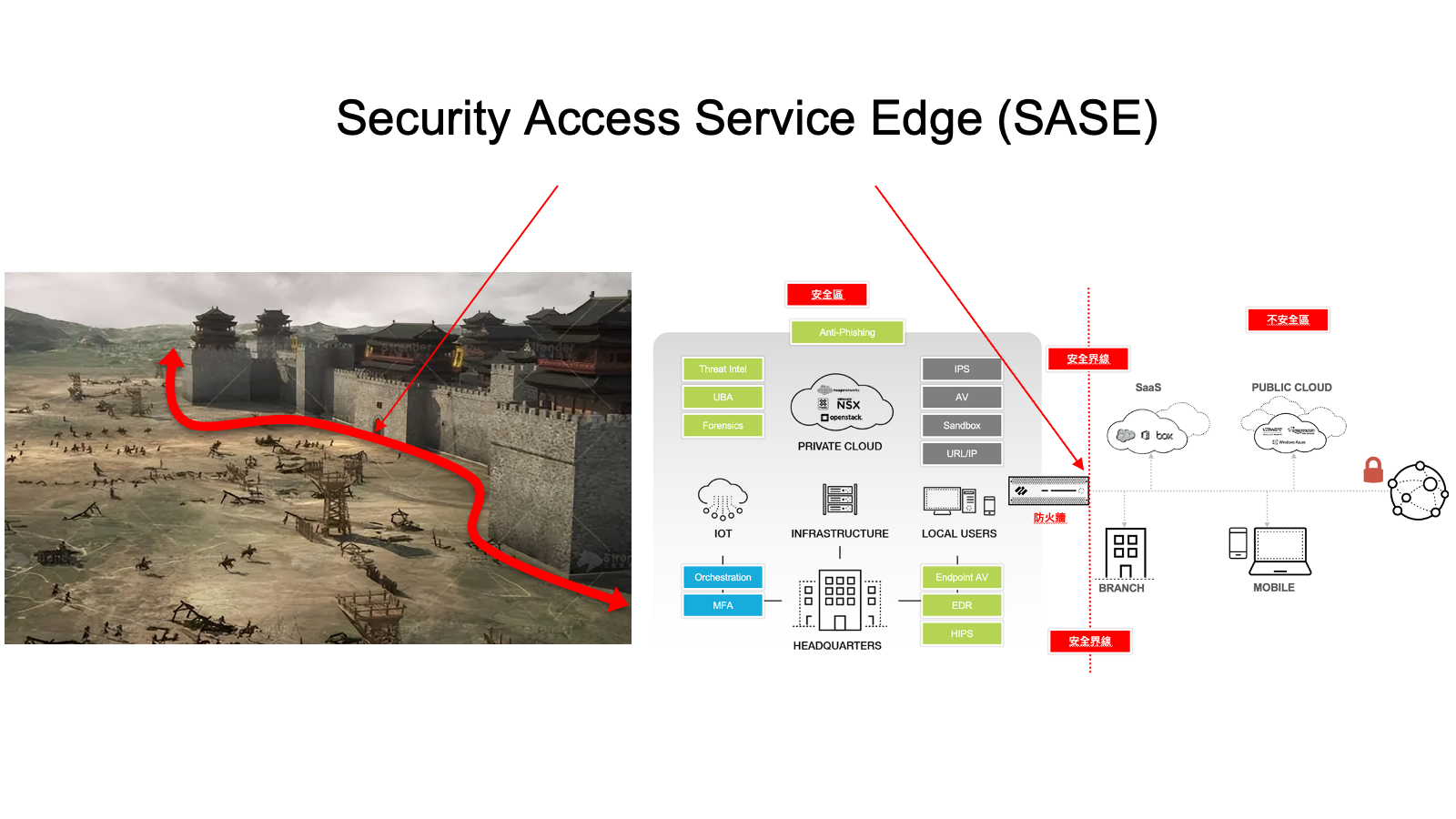
What is SASE?
Security Access Service Edge
Prisma SASE:
A platform that continuously protects mobile users, remote offices, and web security.
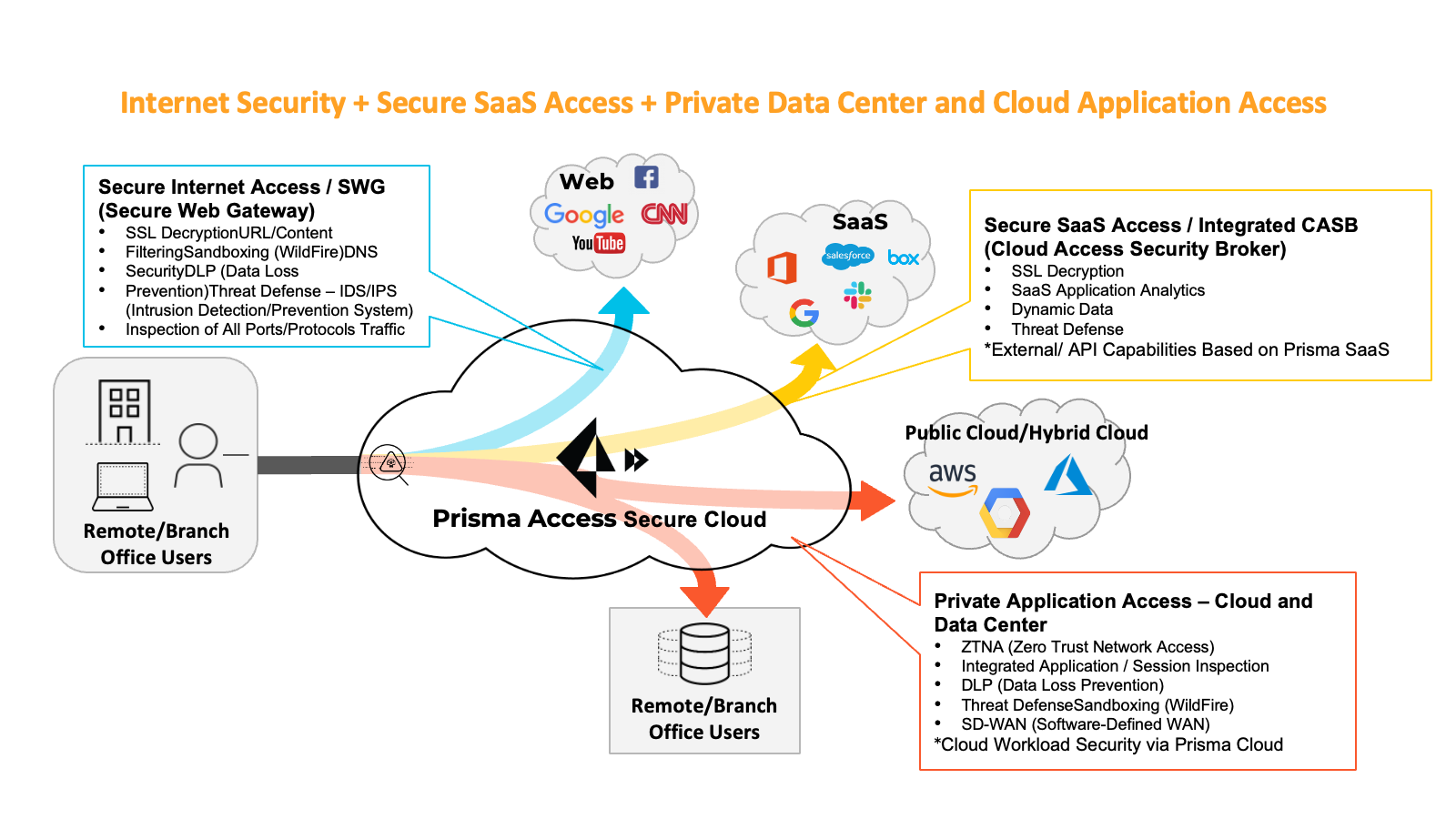
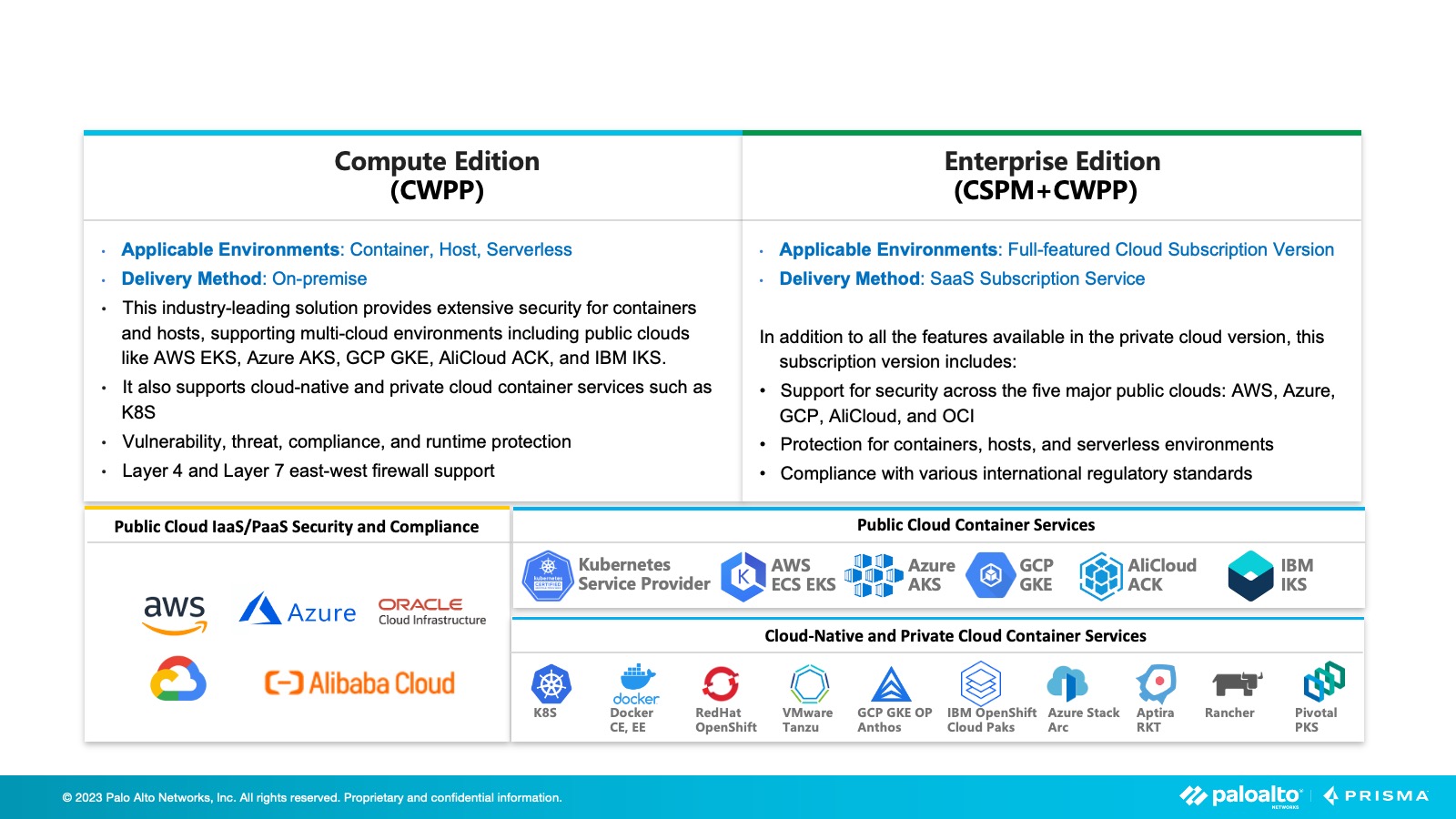
PRISMA ACCESS Product Components
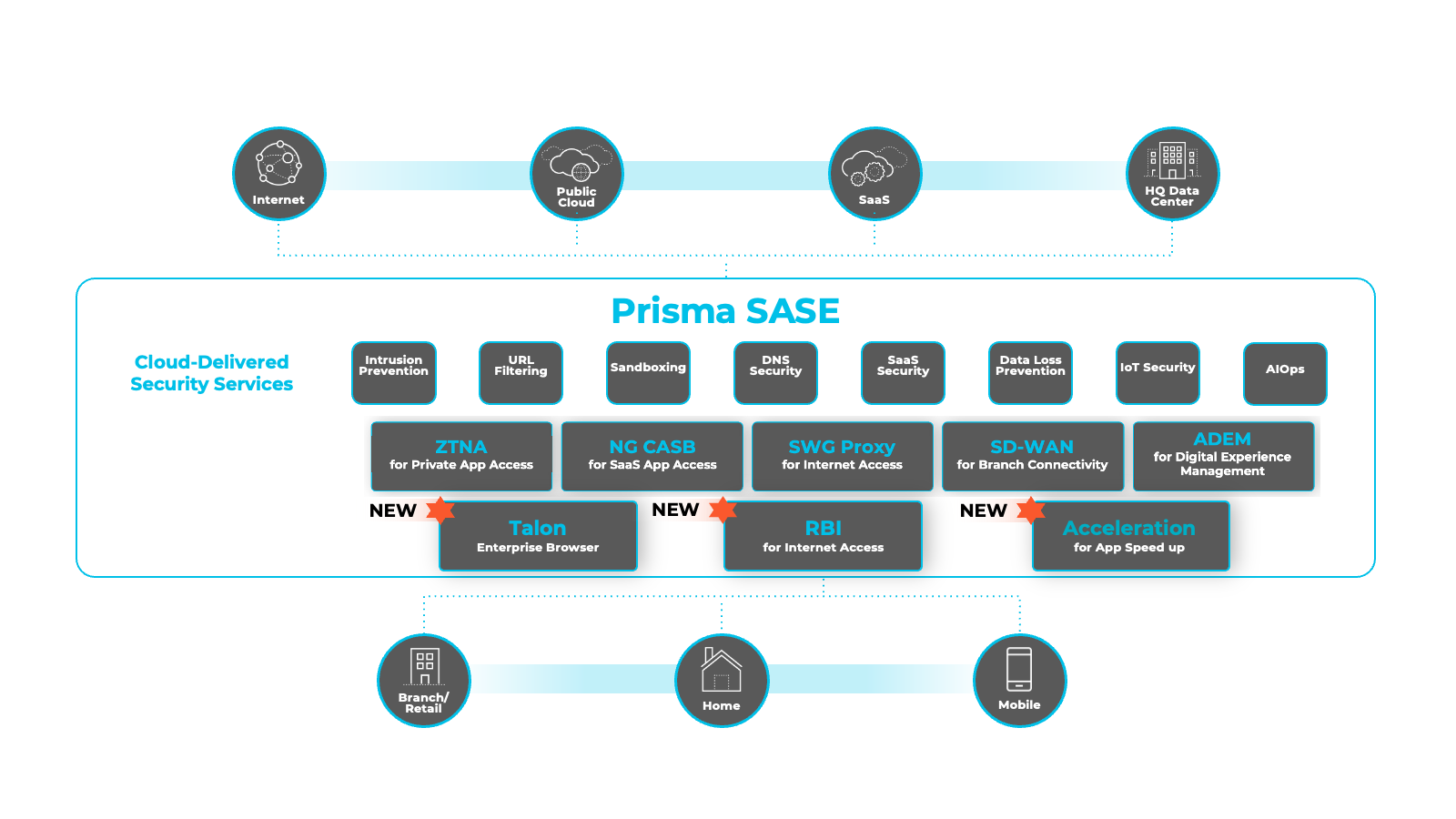
Unified SASE Solution
Integrates security and network functions into a single cloud service. Supports distributed work environments and adapts to the needs of modern enterprises.
Comprehensive Security Protection
Provides comprehensive security features, including Zero Trust Network Access (ZTNA), network firewall, threat protection, and Data Loss Prevention (DLP). Utilizes a global threat intelligence network for real-time threat detection and defense.
Simplified Network Management
Centralize network and security policy management and monitoring through a cloud platform. Supports automated policy deployment to reduce manual configuration and errors.
Efficient User Experience
Provides fast and secure network connectivity, ensuring seamless access to applications and data. Utilizes optimization technologies to enhance application performance, reduce latency, and improve productivity.
Zero Trust Architecture
Adopts Zero Trust principles, requiring all users and devices to be verified before accessing the network. Dynamically adjusts access permissions based on real-time risk assessments for security control.
Flexible Deployment Options
Supports various deployment models to meet diverse enterprise needs, including cloud, hybrid, and on-premises deployments. Compatible with a range of devices and operating systems, providing comprehensive user coverage.
Simplified Compliance Management
Pre-configured with various compliance frameworks to help enterprises quickly meet regulatory requirements. Provides detailed compliance reports and audit capabilities, reducing the burden of compliance management.
Integrated Threat Intelligence
Utilizes global threat intelligence and behavioral analysis technologies for precise threat detection and defense. Provides real-time threat intelligence updates to ensure businesses are always protected with the latest defenses.
Efficient IT Operations
Offers a unified management interface to simplify network and security operations. Supports automated operations and troubleshooting to accelerate problem resolution.





